Core Concepts
Reference
Troubleshooting
Feedback
Roles & Permissions
Organization
Aptible organizations represent an administrative domain consisting of users and resources.
Users
Users represent individuals or robots with access to your organization. A user's assigned roles determine their permissions and what they can access Aptible. Manage users in the Aptible dashboard by navigating to Settings > Members.
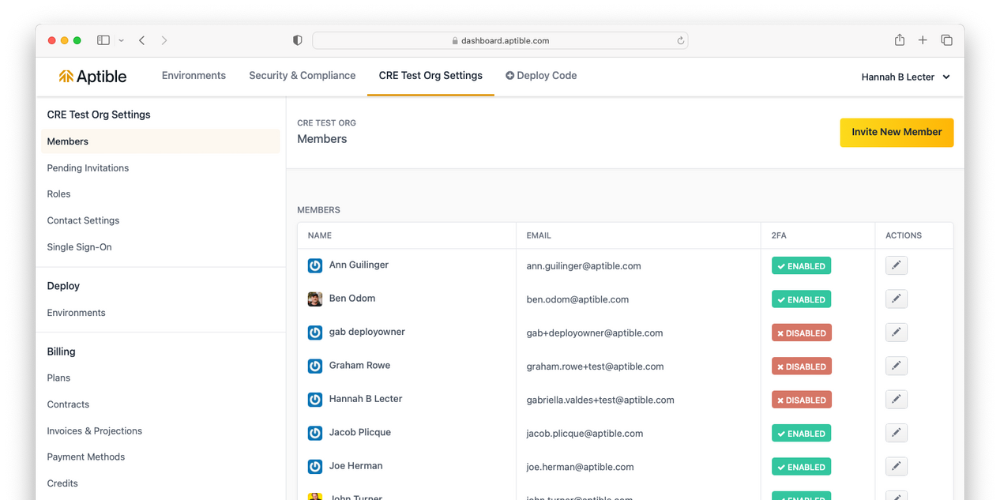
Roles
Use roles to define users' access in your Aptible organization. Manage roles in the Aptible Dashboard by navigating to Settings > Roles.
.png)
Types of Roles
Account Owners
The Account Owners Role is one of the built-in roles in your organization that grants the following:
- admin access to all resources
- access to billing information such as invoices, projections, plans, and contracts
- the ability to invite users
- the ability to manage all Roles
- the ability to remove all users from the organization
Aptible Deploy Owners
The Deploy Owners Role is one of the built-in roles in your organization that grants the following:
- admin access to all resources
- the ability to invite users
- the ability to manage the Aptible Deploy Owners Role and Custom Roles
- the ability to remove users within Aptible Deploy Owners Role and/or Custom Roles from the organization
Custom Roles
Use custom roles to configure which Aptible environments a user can access and what permissions they have within those environments. Aptible provides many permission types so you can fine-tune user access.
Since roles define what environments users can access, we highly recommend using multiple environments and roles to ensure you are granting access based on the least-privilege principle.
Custom Role Admin
The Custom Role Admin role is an optional role that grants:
- access to resources as defined by the permission types of their custom role
- the ability to add new users to the custom roles of which they are role admins
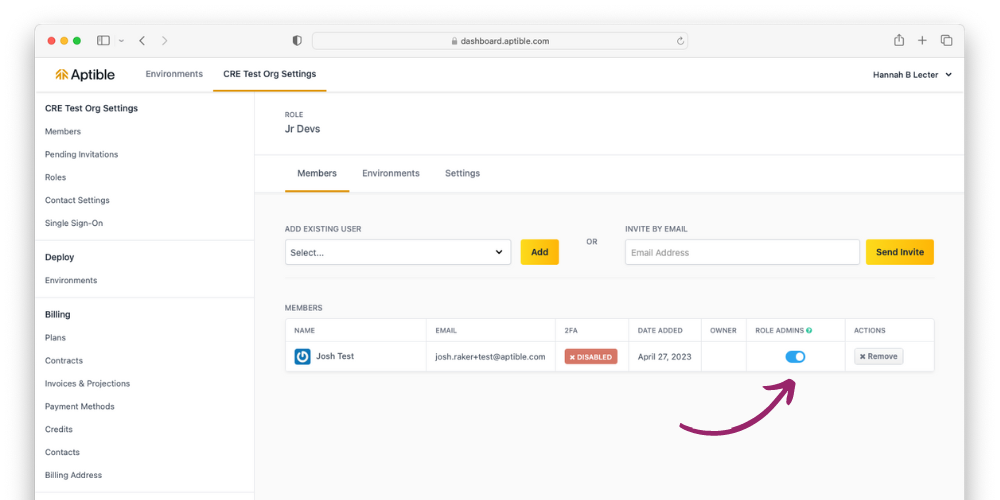
Custom Role Members
Custom Role Members have access to resources as defined by the permission types of their custom role.
Custom Role Permissions
Manage custom role permission types in the Aptible Dashboard by navigating to Settings > Roles. Select the respective role, navigate to Environments, and grant the desired permissions for the separate environments.
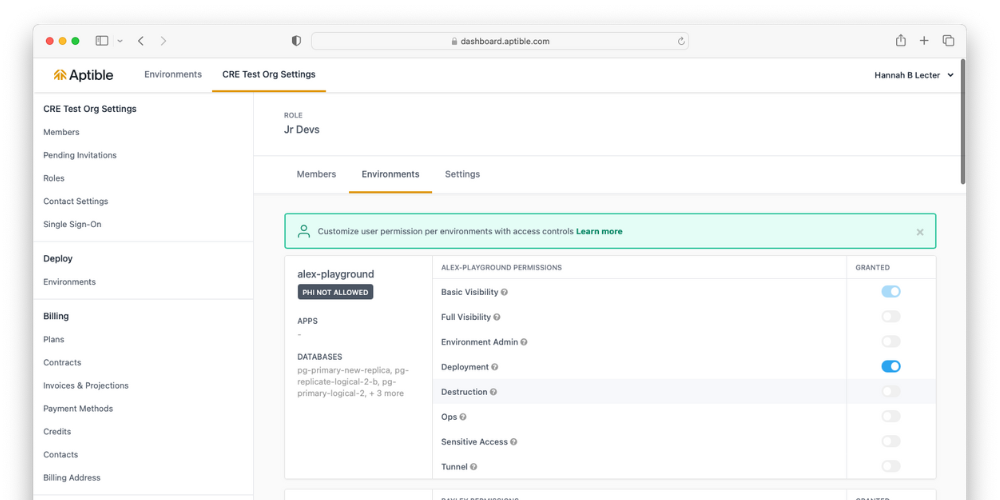
Read Permissions
Assign one of the following permissions to give users read permission in a specific environment:
- Basic Visibility: can read general information about all resources
- Full Visibility (formerly Read): can read general information about all resources and app configurations
Write Permissions
To give users write permission to a given environment, you can assign the following permissions:
- Environment Admin (formerly Write): can perform all actions listed below within the environment
- Deployment: can create and deploy resources
- Destruction: can destroy resources
- Ops: can create and manage log and metric drains and restart and scale apps and databases
- Sensitive Access: can view and manage sensitive values such as app configurations, database credentials, and endpoint certificates
- Tunnel: can tunnel into databases but cannot view database credentials
📘 Provide read-only database access by granting the Tunnel permission without the Sensitive Access permission. Use this to manage read-only database access within the database itself.
Full Permission Type Matrix
This matrix describes the required permission (header) for actions available for a given resource(left column).
| Environment Admin | Full Visibility | Deployment | Destruction | Ops | Sensitive Access | Tunnel | |
|---|---|---|---|---|---|---|---|
| Environment | --- | --- | --- | --- | --- | --- | --- |
| Deprovision | ✔ | ✔ | |||||
| Rename | ✔ | ||||||
| Manage Backup Retention Policy | ✔ | ||||||
| Apps | Environment Admin | Full Visibility | Deployment | Destruction | Ops | Sensitive Access | Tunnel |
| Create | ✔ | ✔ | ✔ | ||||
| Deprovision | ✔ | ✔ | |||||
| Read Configuration | ✔ | ✔ | ✔ | ||||
| Configure | ✔ | ✔ | ✔ | ||||
| Rename | ✔ | ✔ | |||||
| Deploy | ✔ | ✔ | |||||
| Rebuild | ✔ | ✔ | |||||
| Scale | ✔ | ✔ | ✔ | ||||
| Restart | ✔ | ✔ | ✔ | ||||
| Create Endpoints | ✔ | ✔ | |||||
| Deprovision Endpoints | ✔ | ✔ | |||||
| Stream Logs | ✔ | ✔ | ✔ | ||||
| SSH/Execute | ✔ | ✔ | |||||
| Scan Image | ✔ | ✔ | ✔ | ||||
| Databases | Environment Admin | Full Visibility | Deployment | Destruction | Ops | Sensitive Access | Tunnel |
| Create | ✔ | ✔ | |||||
| Deprovision | ✔ | ✔ | |||||
| Read Credentials | ✔ | ✔ | |||||
| Create Backups | ✔ | ✔ | ✔ | ||||
| Restore Backups | ✔ | ✔ | |||||
| Purge Backups | ✔ | ✔ | |||||
| Rename | ✔ | ✔ | |||||
| Restart / Reload / Modify | ✔ | ✔ | ✔ | ||||
| Create Replicas | ✔ | ✔ | |||||
| Create Endpoints | ✔ | ✔ | |||||
| Deprovision Endpoints | ✔ | ✔ | |||||
| Create Tunnels | ✔ | ✔ | |||||
| Stream Logs | ✔ | ✔ | ✔ | ||||
| Log and Metric Drains | Environment Admin | Full Visibility | Deployment | Destruction | Ops | Sensitive Access | Tunnel |
| Create | ✔ | ✔ | ✔ | ||||
| Deprovision | ✔ | ✔ | ✔ | ✔ | |||
| SSL Certificates | Environment Admin | Full Visibility | Deployment | Destruction | Ops | Sensitive Access | Tunnel |
| Create | ✔ | ✔ | |||||
| Delete | ✔ | ✔ | ✔ |